Why Data Backup is Important? | The Vital Role of Data Backup

Data backup is essential because it protects against data loss, ensuring you can recover vital information in case of hardware failures, cyberattacks, accidental deletions, or natural disasters. Regular backups safeguard critical data, minimize downtime, and maintain business continuity, providing peace of mind that your data is secure and retrievable when needed.
How to Set up a Small Business Computer Network?

Establishing a small business computer network involves several key steps. Begin by assessing your needs and selecting appropriate hardware, including routers, switches, and access points. Plan the network layout, considering cable routes and equipment placement. Prioritize network security by enabling firewalls, setting strong passwords, and implementing antivirus software. Define user access levels and establish network policies. Test and optimize the network for performance and reliability.
What Technique Can Improve Web Search Results?
In the quest for improved web search results, various techniques play a crucial role in optimizing the user experience. One notable method involves leveraging machine learning algorithms to refine search queries and deliver more relevant results. By analyzing user behavior and preferences, these algorithms can dynamically adjust search rankings, leading to a more personalized and accurate search experience.
What is Software Infrastructure? | Key Concept of Software Infrastructure

Embark on a journey to unravel the intricate realm of software infrastructure with our comprehensive guide. From the basic building blocks to the intricate web of interconnected systems, we delve into the core components that form the backbone of modern software applications. Explore the significance of robust infrastructure in ensuring seamless operation, scalability, and security in today’s digital landscape.
Which of the Following Provides Security for Wireless Networks?

This post explores key security measures for wireless networks. It begins by emphasizing the importance of encryption protocols like WPA2, WPA3, and AES in securing data transmission. Authentication mechanisms such as PSK and EAP are discussed for verifying user and device identities. Additionally, the role of Intrusion Detection and Prevention Systems (IDPS) in proactive threat management is highlighted.
What is UX strategy? | Understanding UX Strategy

UX strategy involves creating a roadmap to ensure that user experience (UX) design aligns with business goals and user needs. It encompasses defining objectives, understanding users, and outlining methods to achieve desired outcomes. A successful UX strategy integrates market research, user feedback, and business objectives to inform design decisions. It focuses on delivering a seamless and satisfying user experience across all touchpoints, including websites, applications, and physical products.
What Hardware do You Need for VOIP? | VOIP Hardwares

Serves as a comprehensive guide to the hardware essentials required for implementing Voice over Internet Protocol (VoIP) systems. It covers the foundational components necessary for both residential and business VoIP setups. These include a high-speed internet connection for clear voice quality, specialized VoIP phones or adapters, and Analog Telephone Adapters (ATAs) for integrating traditional analog phones. For businesses, an IP PBX system is crucial as a central hub for managing VoIP calls internally.
What are The Main Components in a Network?
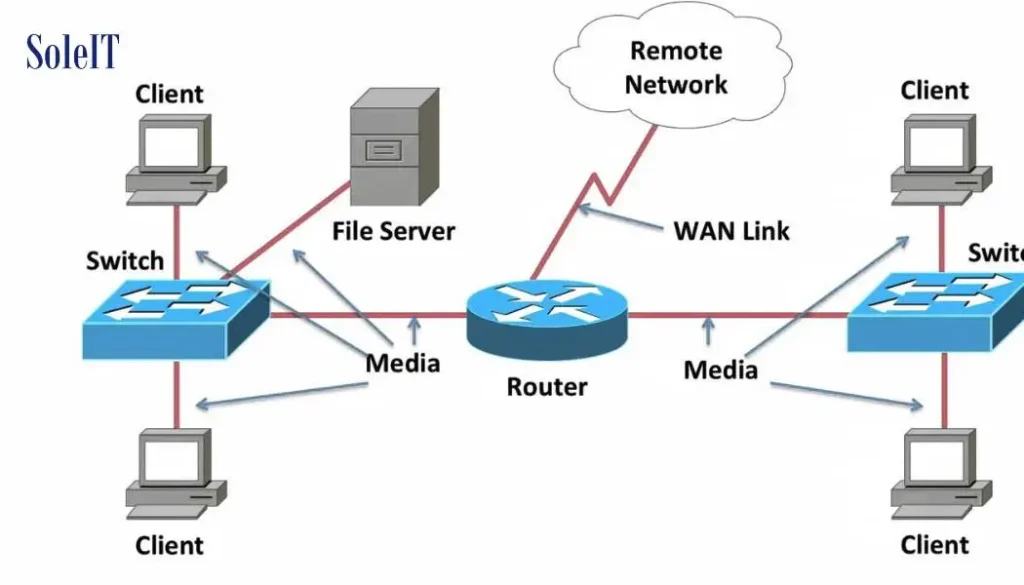
The author discusses the significance of network topology in determining how devices are interconnected and the implications for data transmission efficiency and network resilience. Additionally, the post highlights the importance of network security measures, such as firewalls and encryption protocols, in safeguarding data integrity and protecting against unauthorized access. Furthermore, the post emphasizes the role of network management tools and software applications in monitoring and optimizing network performance.
Why is Vendor Risk Management Important?

Vendor risk management is a critical aspect of business operations that cannot be overlooked. With the increasing reliance on third-party vendors for various services and products, companies are exposed to a myriad of risks that could have severe repercussions if not managed effectively. Firstly, vendor risk management ensures the security and integrity of data and assets entrusted to external parties.
Is SEO a Marketing Channel? | Understanding SEO’s Place

The post delves into the question of whether SEO (Search Engine Optimization) should be considered a marketing channel in the digital landscape. It starts by defining SEO as the practice of optimizing websites to rank higher in search engine results pages (SERPs) and discusses its importance in driving organic traffic to websites. The article explores how SEO fits into the broader spectrum of digital marketing channels, comparing it to other channels such as social media, email marketing, and paid advertising.
